2.10 Struct2
简介
Struts2是一个基于MVC设计模式的Web应用框架,它本质上相当于一个servlet,在MVC设计模式中,Struts2作为控制器(Controller)来建立模型与视图的数据交互。Struts 2是Struts的下一代产品,是在 struts 1和WebWork的技术基础上进行了合并的全新的Struts 2框架。其全新的Struts 2的体系结构与Struts 1的体系结构差别巨大。Struts 2以WebWork为核心,采用拦截器的机制来处理用户的请求,这样的设计也使得业务逻辑控制器能够与ServletAPI完全脱离开,所以Struts 2可以理解为WebWork的更新产品。虽然从Struts 1到Struts 2有着太大的变化,但是相对于WebWork,Struts 2的变化很小。
s2-001
影响版本
Struts 2.0.0 - Struts 2.0.8
漏洞简介
该漏洞因为用户提交表单数据并且验证失败时,后端会将用户之前提交的参数值使用 OGNL 表达式 %{value} 进行解析,然后重新填充到对应的表单数据中。例如注册或登录页面,提交失败后端一般会默认返回之前提交的数据,由于后端使用 %{value} 对提交的数据执行了一次 OGNL 表达式解析,所以可以直接构造 Payload 进行命令执行
漏洞复现
首先打开漏洞界面
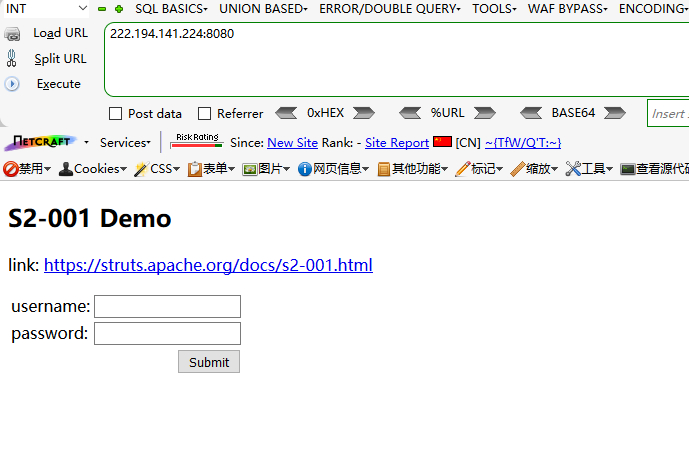
Get the tomcat path:
Get the web site real path:
Execute command (command with parameter:new java.lang.String[]{"cat","/etc/passwd"}):
s2-005
影响版本
2.0.0-2.1.8.1
漏洞简介
通过unicode 编码 \u0023 绕过struts对#的过滤,再通过设置xwork.MethodAccessor.denyMethodExecution 为false 和memberAccess.allowStaticMethodAccess为true 来绕过沙盒
漏洞复现

获取信息(k8)

poc:
s2-007
影响版本
2.0.0-2.2.3
漏洞成因
当配置了验证规则类型转换出错时进行了错误的字符串拼接进而造成了OGNL语句的执行。后端用代码拼接 "'" + value + "'" 然后对其进行 OGNL 表达式解析,比较类似SQL注入单引号闭合,插入语句,官方修复的时候也跟sql注入比较相似,escape 对单引号转义
漏洞复现
poc:
s2-008
影响版本:
2.1.0 - 2.3.1
漏洞成因
主要是利用对传入参数没有严格限制导致多个地方可以执行恶意代码 第一种情况其实就是S2-007在异常处理时的OGNL执行 第二种的cookie的方式虽然在struts2没有对恶意代码进行限制但是java的webserverTomcat对cookie的名称有较多限制在传入struts2之前就被处理从而较为鸡肋 第四种需要开启devModedebug模式
复现采用的是第四种devMode的debug模式造成的任意代码执行
漏洞复现
POC:
s2-009
影响版本
2.1.0 - 2.3.1.1
漏洞成因
这个漏洞跟s2-003 s2-005 属于一套的。 Struts2对s2-003的修复方法是禁止#号于是s2-005通过使用编码\u0023或\43来绕过于是Struts2对s2-005的修复方法是禁止\等特殊符号使用户不能提交反斜线。 但是如果当前action中接受了某个参数example这个参数将进入OGNL的上下文。所以我们可以将OGNL表达式放在example参数中然后使用/HelloWorld.acton?example=&(example)('xxx')=1的方法来执行它从而绕过官方对#、\等特殊字符的防御。
漏洞复现
POC:
s2-012
影响版本:
2.1.0 - 2.3.13
漏洞成因
如果在配置 Action 中 Result 时使用了重定向类型并且还使用 ${param_name} 作为重定向变量例如
这里 UserAction 中定义有一个 name 变量当触发 redirect 类型返回时Struts2 获取使用 ${name} 获取其值在这个过程中会对 name 参数的值执行 OGNL 表达式解析从而可以插入任意 OGNL 表达式导致命令执行。
漏洞复现
POC:
s2-013
影响版本
Struts 2.0.0 - Struts 2.3.14
漏洞成因
struts 的标签中 和 都有一个 includeParams 属性 none - URL中不包含任何参数默认 get - 仅包含URL中的GET参数 all - 在URL中包含GET和POST参数 当includeParams=all的时候会将本次请求的GET和POST参数都放在URL的GET参数上。 明明可以urldecode一下就知道params是啥了但struts给OGNL解析了就造成了任意代码执行
漏洞复现
POC:
s2-015
影响版本
2.0.0 - 2.3.14.2
漏洞成因
基于通配符定义的动作映射如果一个请求跟任何其他定义的操作不匹配他将会匹配*并且请求的同操作名称的jsp文件
http://192.168.95.128:8080/example/HelloWorld.action ==>改成 http://192.168.95.128:8080/example/%{1%2B1}.action
漏洞复现
POC:
s2-016
影响版本
Struts2.0.0 - Struts2.3.15
漏洞成因
DefaultActionMapper类支持以"action:"、"redirect:"、"redirectAction:"作为导航或是重定向前缀但是这些前缀后面同时可以跟OGNL表达式由于struts2没有对这些前缀做过滤导致利用OGNL表达式调用java静态方法执行任意系统命令
漏洞复现
POC:
s2-019
影响版本
Struts 2.0.0 - Struts 2.3.15.1
漏洞成因
漏洞复现
POC:
s2-032
影响版本
Struts 2.3.20 - Struts Struts 2.3.282.3.20.3和2.3.24.3除外
需要开启动态方法调用
使用?method:execute的方式调用execute方法execute方法是struts2中默认的action调用方法在method:后面加上我们要执行的ognl表达式即可执行任意代码了
漏洞复现
s2-033
影响版本
Struts 2.3.20 - Struts Struts 2.3.282.3.20.3和2.3.24.3除外
漏洞复现
POC
s2-037 CVE-2016-4438
漏洞版本
Struts 2.3.20 - Struts Struts 2.3.282.3.20.3和2.3.24.3除外
漏洞成因
和S2-033一样也是关于rest插件导致method变量被篡改造成的远程代码执行漏洞这个漏洞和之前S2-033是一个地方都是在DefaultActionInvocation.java的invokeAction方法中没有对于methodName参数内容进行校验便直接丢到了getValue方法里面从而造成Ongl表达式的注入。
漏洞复现
s2-045 CVE-2017-5638
漏洞版本
2.3.31-2.3.5 2.5-2.5.10 和046类似只是攻击字段发生变化 045是Content-Type 046是filname
漏洞复现
exp:
s2-046 CVE-2017-5638
影响版本
2.3.5-2.3.31 2.5.0-2.5.10
漏洞成因
使用Jakarta插件程序没有正确处理文件上传通过构造HTTP请求头中的Content-type造成RCE
常见访问路径
/struts2-showcase/fileupload/doUpload.action /doUpload.action /
漏洞复现
抓流量 抓到一个 出web目录的 后面自己加\x00b
RCE
s2-048 CVE-2017-9791
影响版本
2.3.x
漏洞成因
当实用了Struts2 Struts1 插件时可能导致不受信任的输入传入到ActionMessage类种导致命令执行
漏洞复现
s2-052 CVE-2017-9805
影响版本
Struts 2.1.2 - Struts 2.3.33, Struts 2.5 - Struts 2.5.12
漏洞成因
Struts2-Rest-Plugin是让Struts2能够实现Restful API的一个插件其根据Content-Type或URI扩展名来判断用户传入的
漏洞复现
s2-053 CVE-2017-12611
影响版本
Struts 2.0.1 - Struts 2.3.33, Struts 2.5 - Struts 2.5.10
漏洞成因
Struts2在使用Freemarker模板引擎的时候同时允许解析OGNL表达式。导致用户输入的数据本身不会被OGNL解析但由于被Freemarker解析一次后变成离开一个表达式被OGNL解析第二次导致任意命令执行漏洞。
漏洞复现
s2-057 CVE-2018-11776
影响版本:
小于等于 Struts 2.3.34 与 Struts 2.5.16
漏洞原因
当Struts2的配置满足以下条件时
alwaysSelectFullNamespace值为true action元素未设置namespace属性或使用了通配符 namespace将由用户从uri传入并作为OGNL表达式计算最终造成任意命令执行漏洞。 http://127.0.0.1:8080/${1+1}/actionChain1.action ===> http://127.0.0.1:8080/2/register2.action
漏洞复现
相关工具
st2全版本漏洞扫描:
k8 st2漏洞利用:
Last updated
Was this helpful?